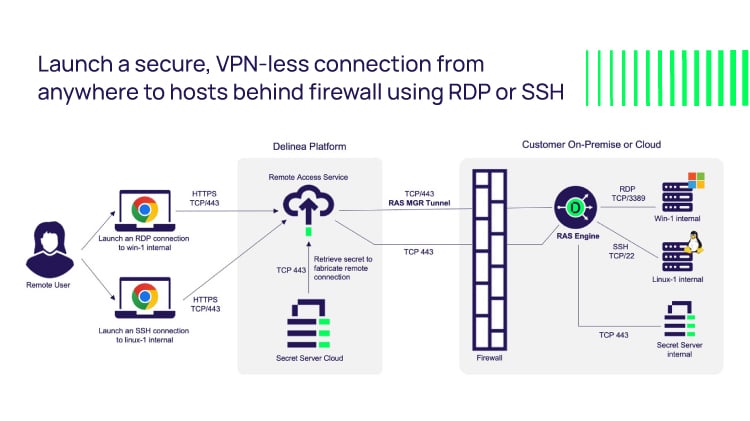
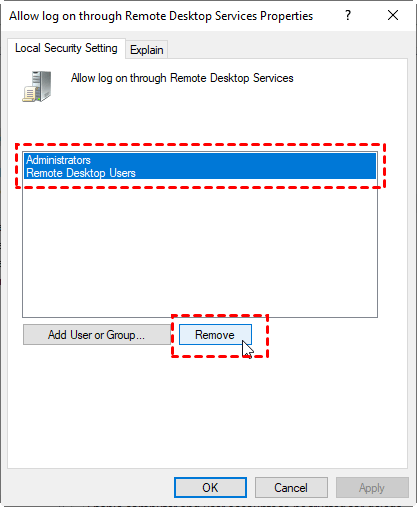
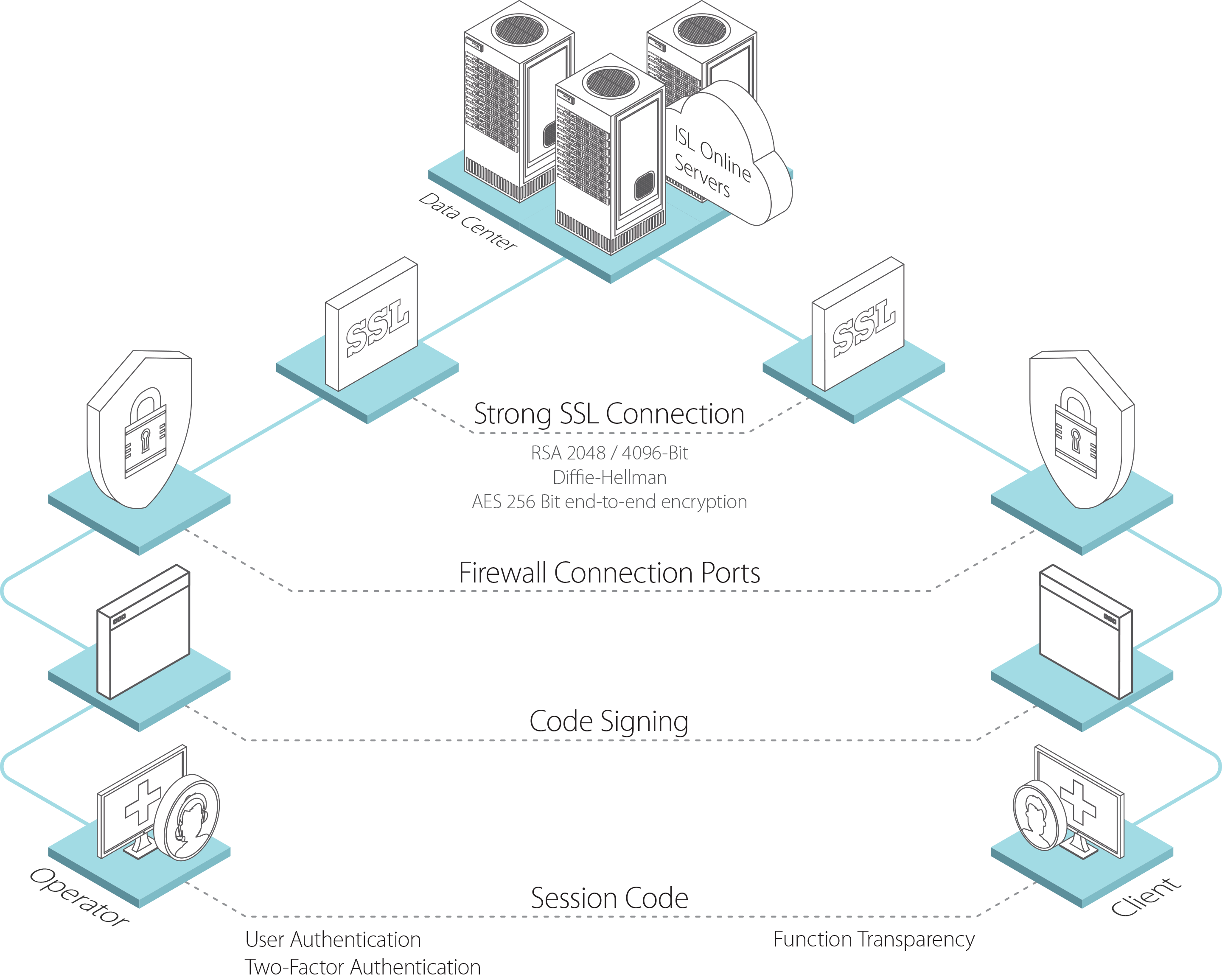
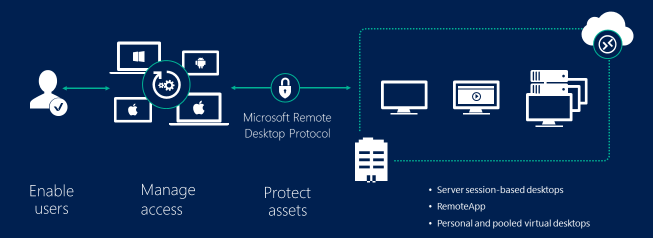
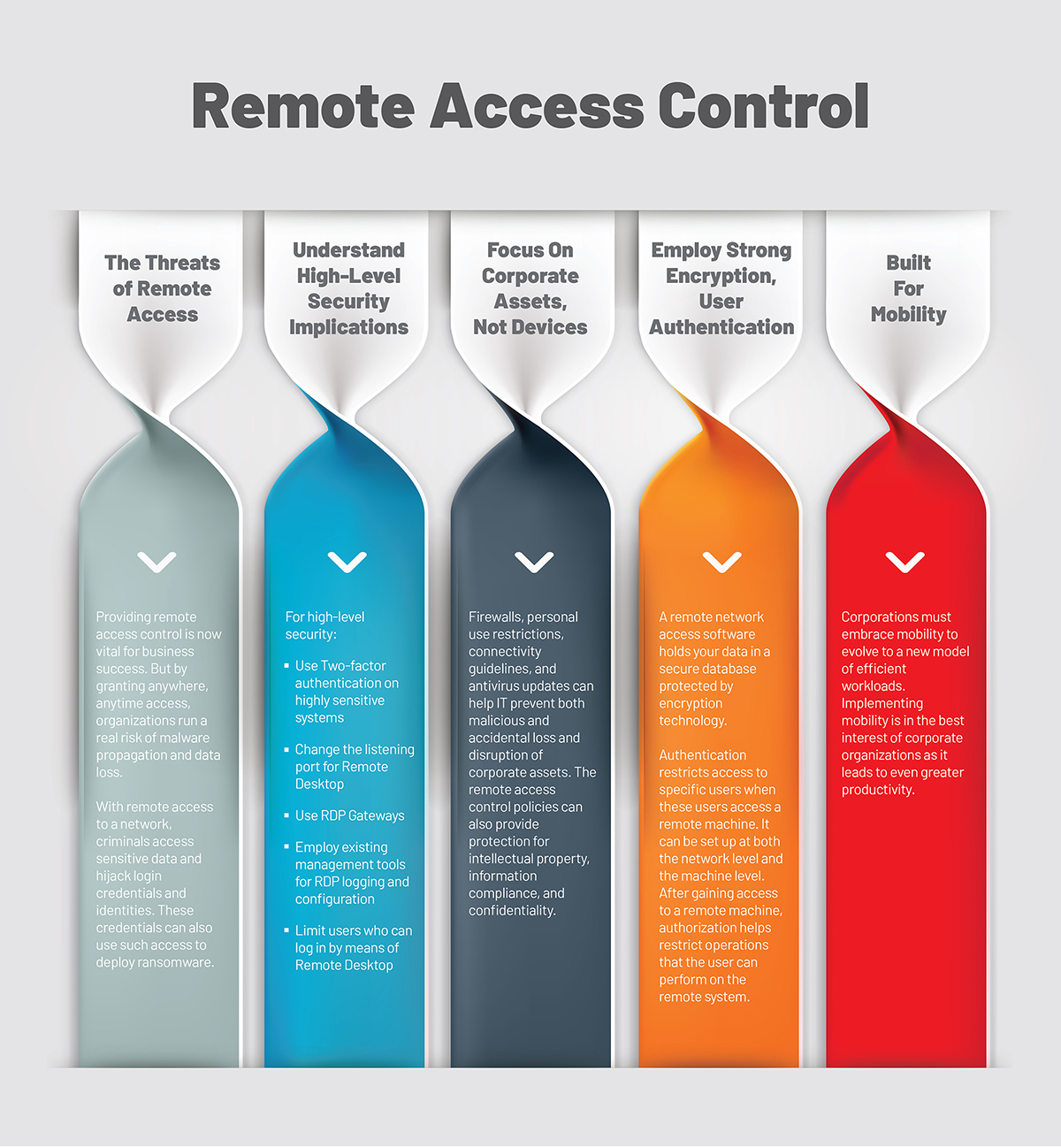
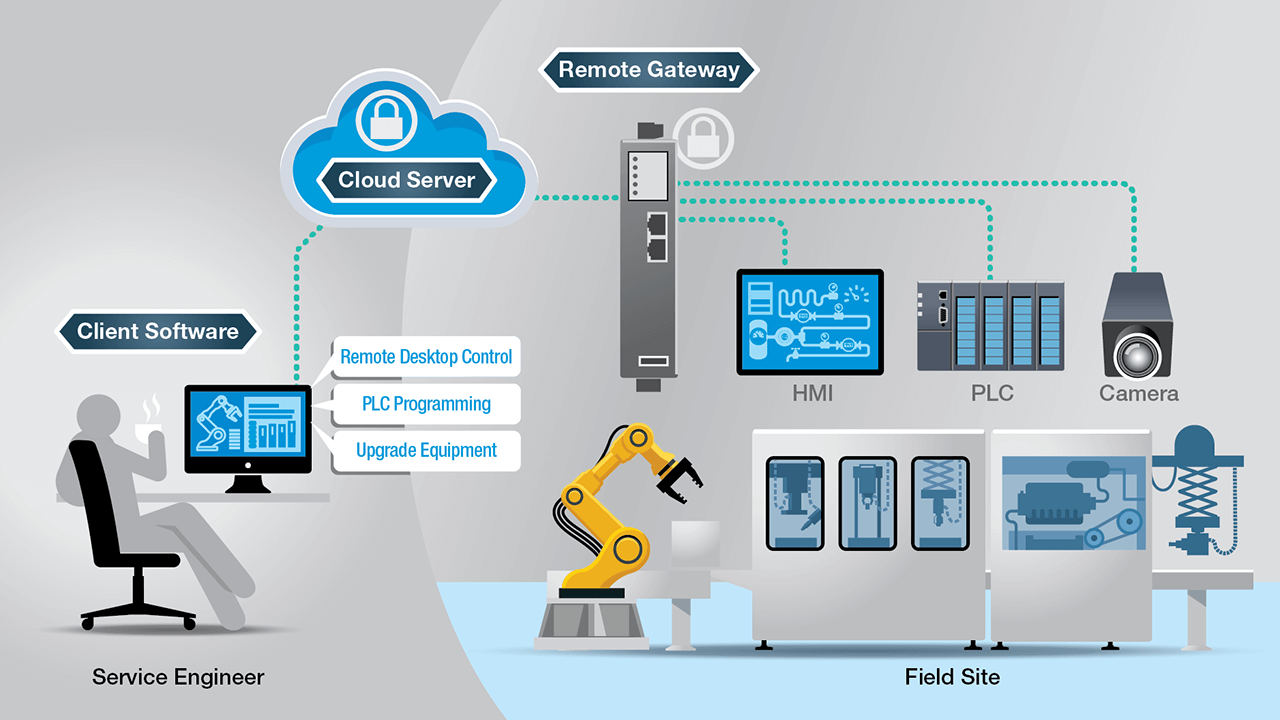
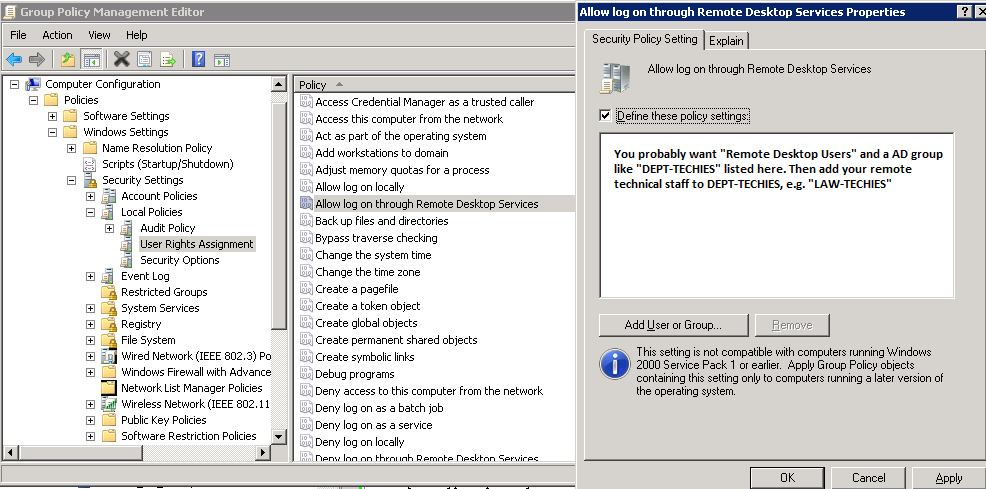
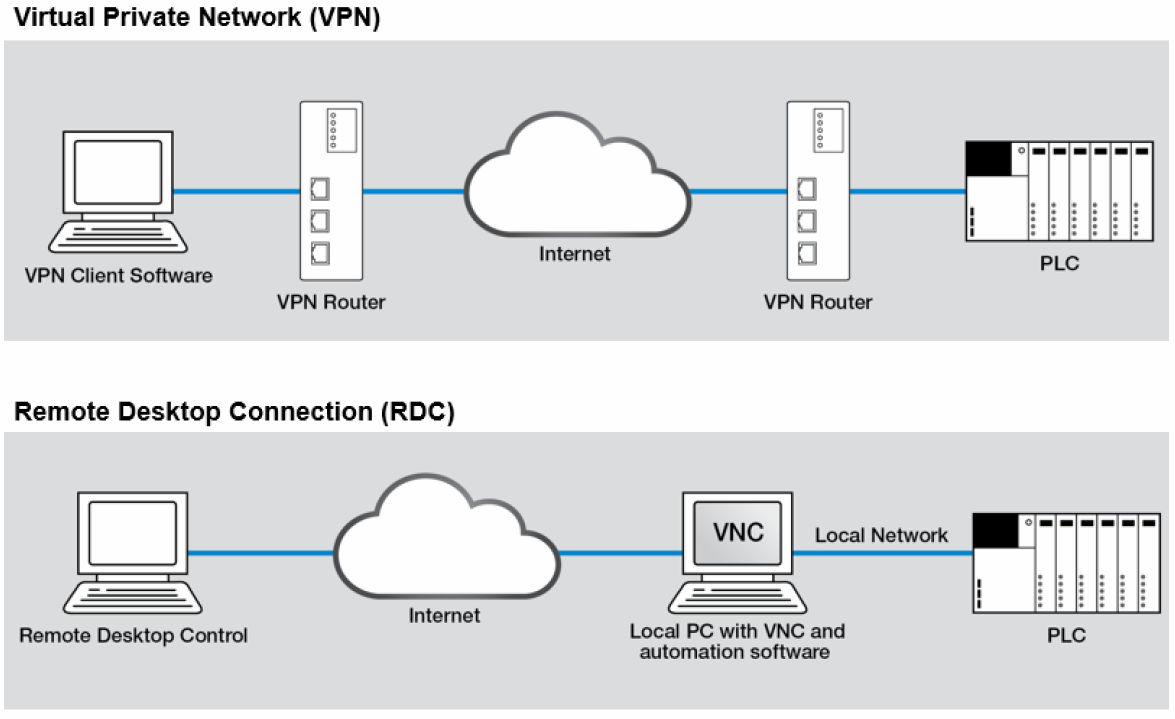
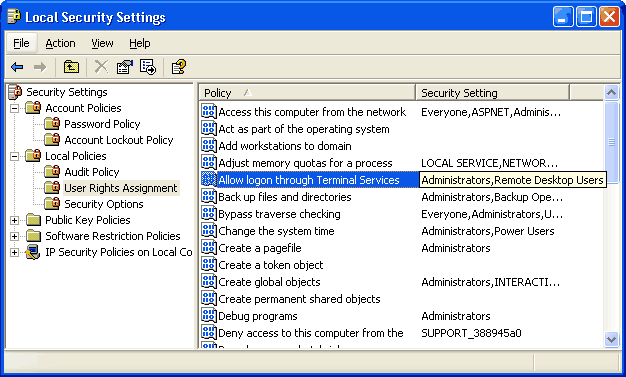
Remote desktop protocol (RDP) is a secure network communications protocol developed by Microsoft. | by Tezrdp | Medium

The Ultimate Guide to Secure Remote Desktop Connections To Safely Access Your PC over the Internet - YouTube

Secure remote access: What it is, importance, benefits, and best practices | ManageEngine Access Manager Plus

IDrive Introduces Remote Desktop - Providing Secure Remote Access to Windows Computers and Servers via RDP