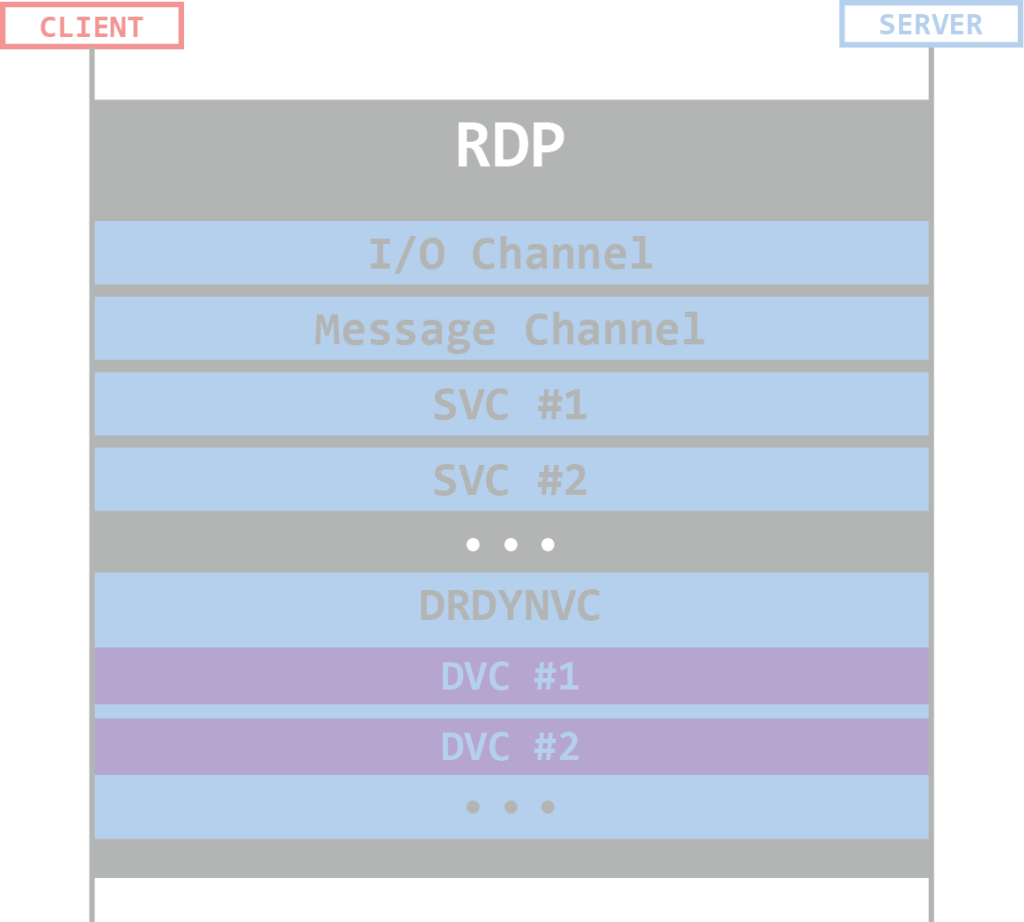
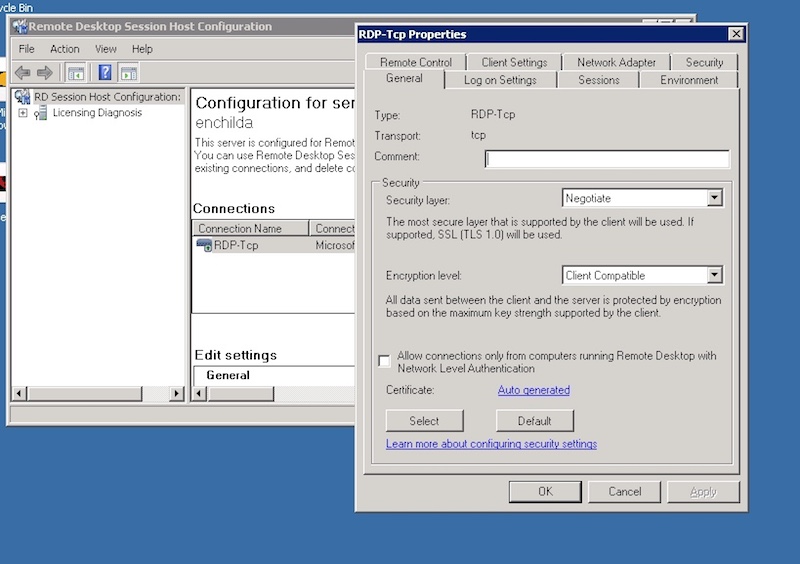
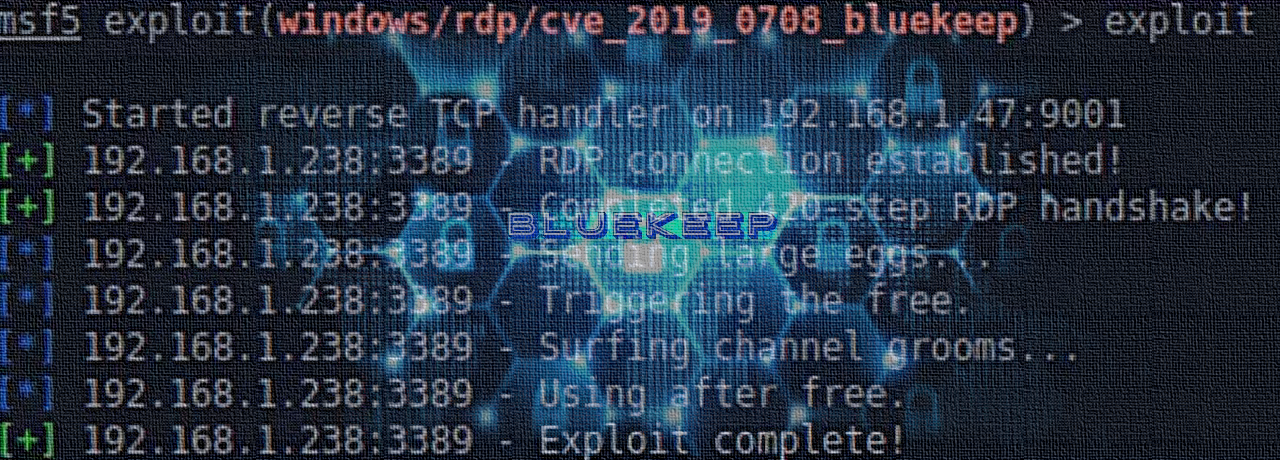
Attack Chain Series: Remote Access Service Compromise Part 1 — RDS | by Vartai Security | Vartai Security | Medium
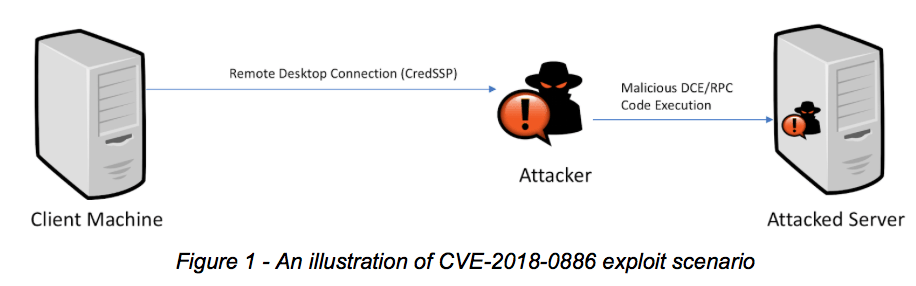
A critical flaw in Credential Security Support Provider protocol (CredSSP) affects all versions of Windows

Attack Chain Series: Remote Access Service Compromise Part 1 — RDS | by Vartai Security | Vartai Security | Medium

Attack Chain Series: Remote Access Service Compromise Part 1 — RDS | by Vartai Security | Vartai Security | Medium




![POC] Windows RDP Vulnerability Exploit POC] Windows RDP Vulnerability Exploit](https://thehackernews.com/images/-lRpjz6TH-Ag/T2NTfgq03SI/AAAAAAAAFQ8/YraGNwdSgjc/s728-rw-ft-e30/%5BPOC%5D+Windows+RDP+Vulnerability+Exploit.jpg)