
PPT - Randomness Extraction and Privacy Amplification with quantum eavesdroppers PowerPoint Presentation - ID:4846836
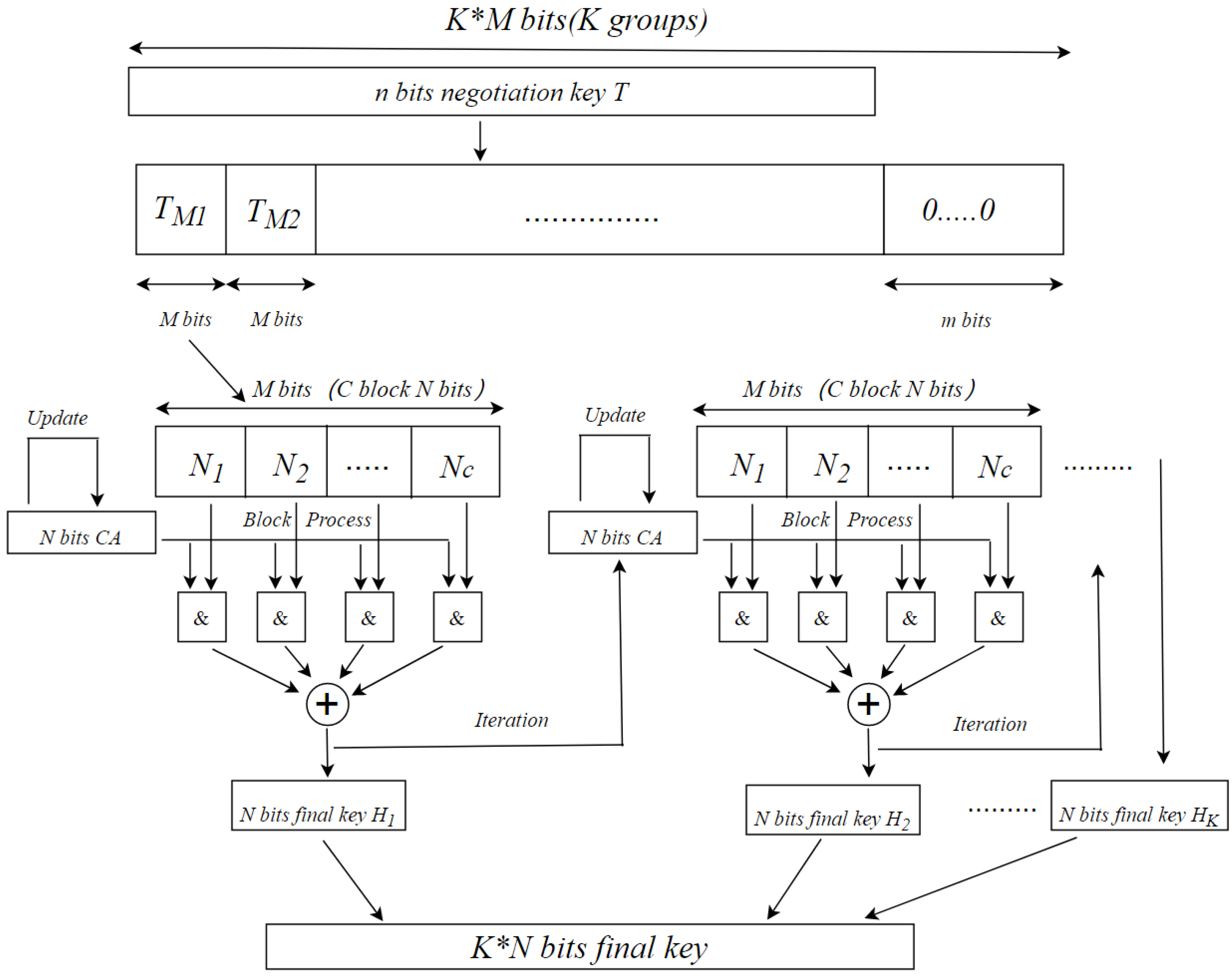
Electronics | Free Full-Text | High-Speed Privacy Amplification Algorithm Using Cellular Automate in Quantum Key Distribution

The process of length-compatible privacy amplification algorithm. The... | Download Scientific Diagram
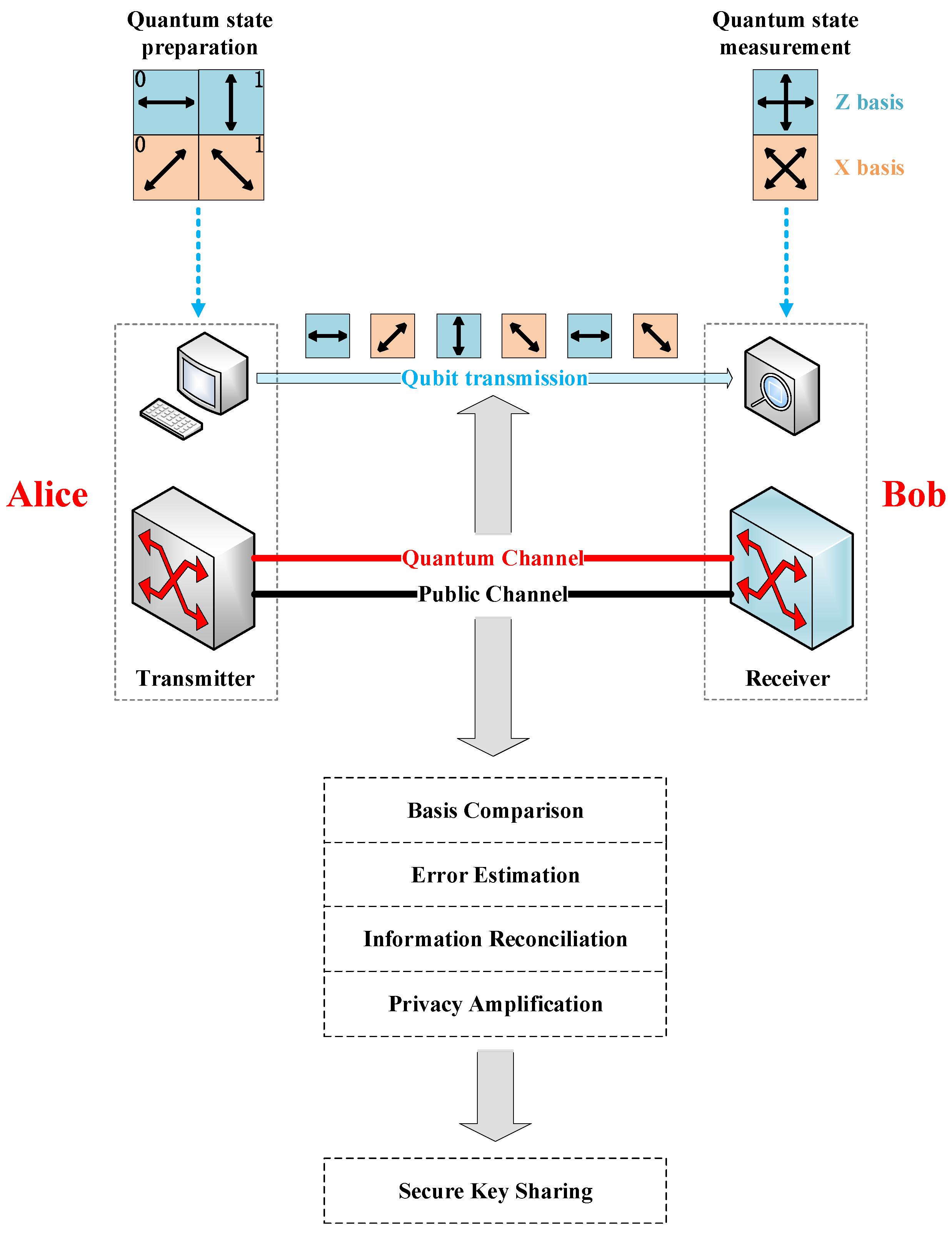
Entropy | Free Full-Text | A Resource-Adaptive Routing Scheme with Wavelength Conflicts in Quantum Key Distribution Optical Networks
High-Speed Implementation of Length-Compatible Privacy Amplification in Continuous-Variable Quantum Key Distribution
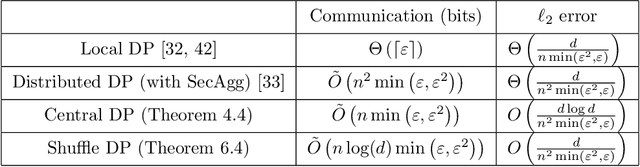
Privacy Amplification via Compression: Achieving the Optimal Privacy-Accuracy-Communication Trade-off in Distributed Mean Estimation: Paper and Code - CatalyzeX

The procedure of accelerating length-compatible privacy amplification... | Download Scientific Diagram

Vitaly 🇺🇦 Feldman on X: "IMO the most significant recent development in privacy preserving data analysis are systems and models that use an anonymizing shuffler. However their formal analysis was rather involved
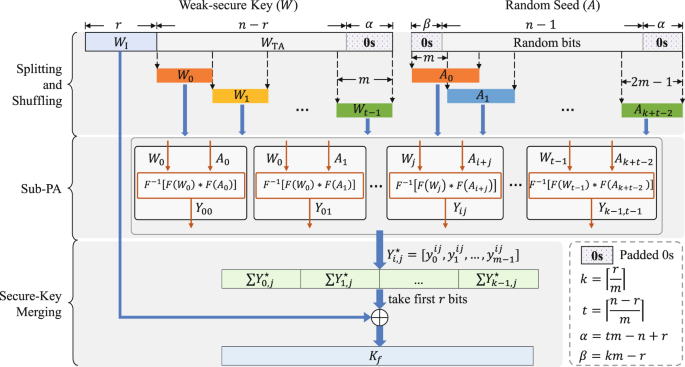
High-speed and Large-scale Privacy Amplification Scheme for Quantum Key Distribution | Scientific Reports

High-speed and Large-scale Privacy Amplification Scheme for Quantum Key Distribution | Scientific Reports
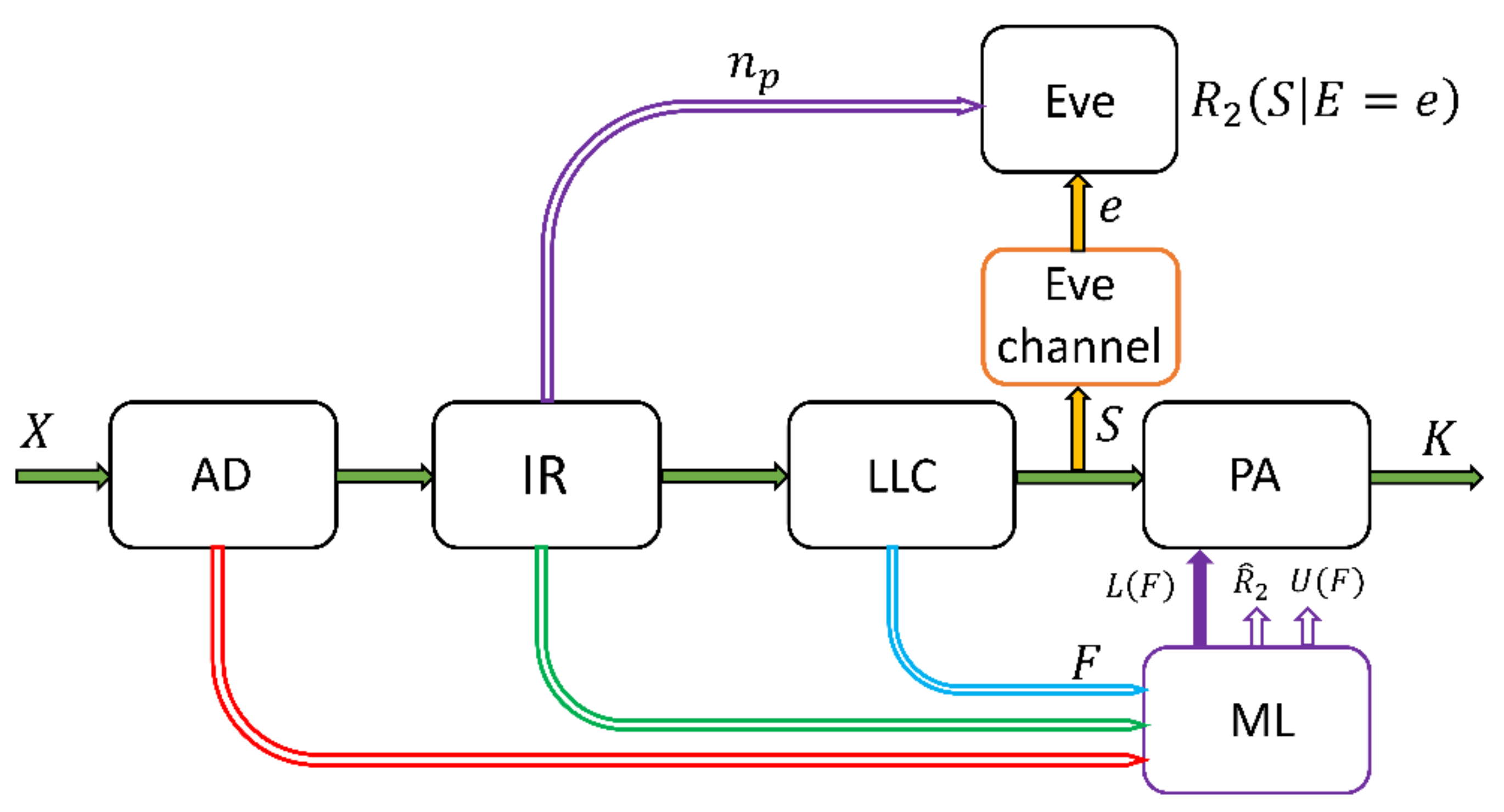
Symmetry | Free Full-Text | Privacy Amplification Strategies in Sequential Secret Key Distillation Protocols Based on Machine Learning

Differences between Extractors and Privacy Amplification for Quantum Random Generators - Cryptography Stack Exchange
![PDF] High-speed Implementation of FFT-based Privacy Amplification on FPGA in Quantum Key Distribution. | Semantic Scholar PDF] High-speed Implementation of FFT-based Privacy Amplification on FPGA in Quantum Key Distribution. | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/00d9158399761b85815dfddbff75a1e12d55017c/3-Figure1-1.png)







